
SCHUTZWERK at Embedded World 2025
February 4, 2025 #news #event #embedded security
SCHUTZWERK visits the Embedded World 2025 in Nuremberg. We are looking forward to your visit!

SCHUTZWERK visits the Embedded World 2025 in Nuremberg. We are looking forward to your visit!

SCHUTZWERK and Lauterbach research new fuzzing and manual pentesting methods to improve the security of embedded and automotive devices.

We from SCHUTZWERK will be at the Embedded World in Nuremberg from April 9th to 11th, 2024! The Embedded World is a trade fair for experts in embedded systems. Come visit our booth 372 in Hall 5 and meet our special companion: Our Glitching Setup, which we use for Fault-Injection attacks as part of Embedded Security Assessments , for example, to bypass security checks like password prompts.

SCHUTZWERK is visiting Munich! From February 21st to 22nd, 2024, we will be at the building IoT Conference participating with a presentation. The building IoT has been the meeting point since 2016 for those developing software applications and digital products in the Internet of Things and Industrial Internet of Things. On February 22nd, in our presentation Breaking Through the Wall: Side Channel Attacks and Fault Injection we will showcase invisible methods through which attackers obtain confidential information.

We are excited to announce that Telechips, a leading supplier of System-on-Chip (SoC) components for automotive In-Vehicle Infotainment and cockpit solutions based in Seoul, South Korea, has selected SCHUTZWERK as their strategic partner for SoC cybersecurity assessments. Telechips has chosen to partner with SCHUTZWERK, a renowned and experienced provider of automotive and embedded security assessments , to conduct comprehensive cybersecurity assessments of their entire SoC portfolio through the end of 2024.

The last part of the PROBoter series showed how innovative algorithms can help an embedded system pentester to analyze recorded voltage signals of an unknown PCB. Besides basic signal characteristics, these algorithms can link signal lines and identify communication buses typically found on PCBs like I2C or SPI. In this final post of the PROBoter series, we draw the big picture of the PROBoter software framework. In parallel to the release of this post, all missing services forming the framework are released on the PROBoter Github repo.

In this whitepaper we summarize some of the security pitfalls device developers should avoid when developing Matter products.

SCHUTZWERK will be at the building IoT conference in Munich from April 26 to 27, 2023 giving a talk. Since 2016, building IoT has been the meeting place for those who develop software applications and digital products in the Internet of Things and the Industrial Internet of Things. On April 27, we will give the talk Easy prey for hackers? Finding and avoiding typical vulnerabilities in IoT solutions , presenting the most common and relevant vulnerabilities in IoT devices from our assessment practice.
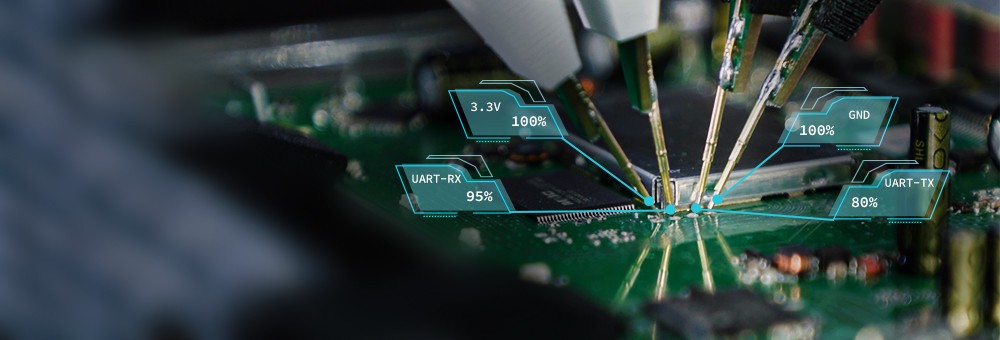
This article is an extension to the SCHUTZWERK blog post series about the PROBoter PCB analysis platform. It introduces the algorithm of the Time Invariant Signal Analysis, which the PROBoter uses to produce information on the functionality of the conducting paths identified on a PCB from passive eavesdropping.

SCHUTZWERK will be present at Embedded World in Nuremberg from March 14-16, 2023. Embedded World is the trade fair for experts along the entire value chain of embedded systems. Visit our booth 4-104c in hall 4 and see our PROBoter in action. We will be happy to present our services in the area of Embedded Security Assessments and explain which vulnerabilities we can uncover from silicon to the cloud.
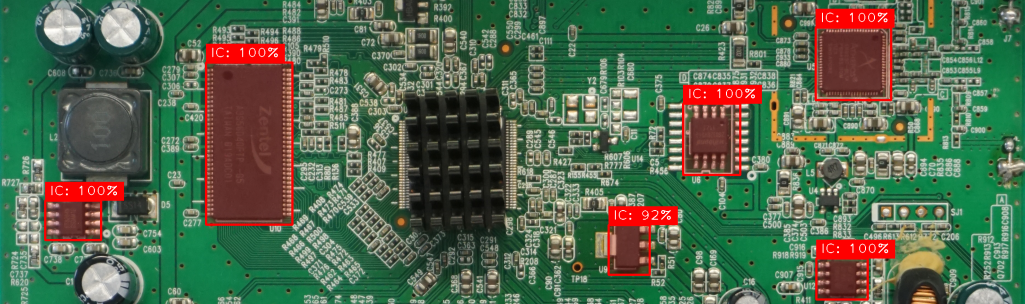
The last part of the PROBoter series introduced the heart of the PROBoter framework - the hardware platform. The platform allows (semi) automated electrical probing of an unknown PCB which is usually a very time consuming and error prone task. This post focuses on methods to automate the initial analysis step of an embedded system - the visual analysis of the PCB(s) forming the device under test.

The PROBoter is a modular, self-calibrating probing machine to support PCB analysis tasks in penetration tests of embedded systems. The video of the PROBoter demonstrates its four main contributions: 1) The automatic visual detection of components and contact points on a PCB, 2) the automatic probing of contact points for net reversing and signal detection, 3) the mapping of signal lines to given bus protocols, and 4) the support in identification of potential attack vectors.
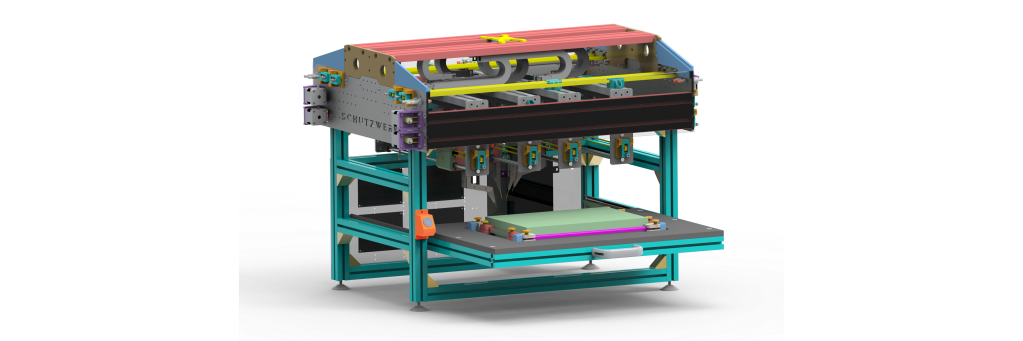
The first part of the PROBoter series gave an introduction to the manual process of embedded system pentesting. It then showed a possible automated workflow which will be implemented in the form of the PROBoter platform. After a longer phase of further internal development and evaluation, this post describes the core component of the PROBoter framework - a hardware platform for automated electrical probing and PCB image generation.
A System-on-a-Chip (SoC) is regularly used in the automotive domain to build electronic control units (ECUs) with high demands on different functionalities and computation power. TeleChips, as a leading supplier of SoC components for automotive In-Vehicle Infotainment and cockpit solutions, chose SCHUTZWERK as an independent and experienced provider for automotive and embedded security assessments to analyze their new SoC series TCC803x (Dolphin+). This success story summarizes the approach and results of the comprehensive security assessment.

In this blog post we present a Bayesian statistical model to detect cryptographic timing attacks. This model is one of the results of a customer hardware assessment performed by the SCHUTZWERK GmbH. The assessment was performed in a gray box context, i.e., we were able to interact with the encryption hardware, but were not given any internal implementation details.

Security analysis of embedded systems on the Printed Circuit Board (PCB) level can be a very tedious and time-consuming task. Many steps like visual PCB inspection and reverse engineering of security relevant nets, i.e. electrically connected components, is usually done manually by an embedded security expert. PROBoter aims at automating this manual analysis.
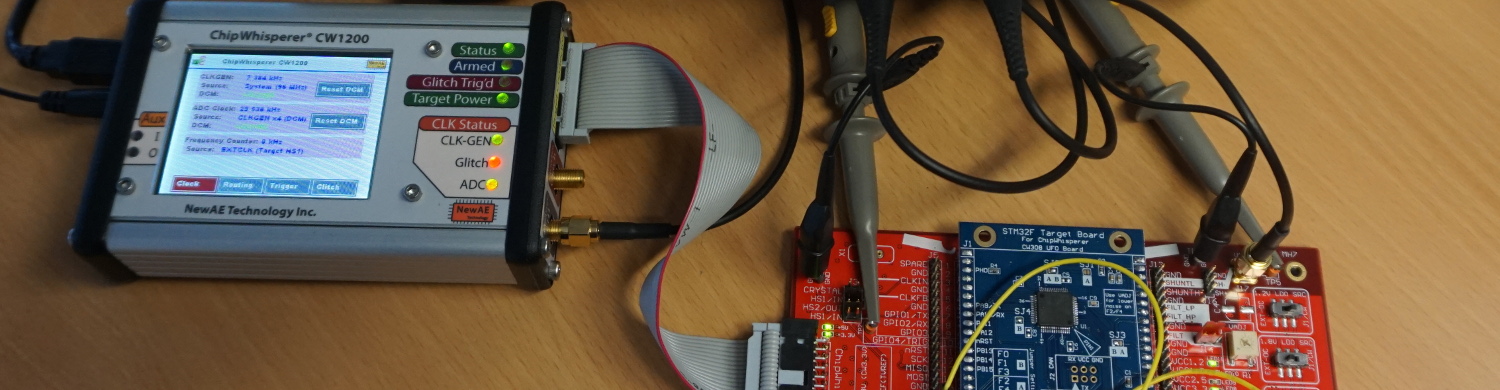
In the previous post a setup and a technique to extract a representative section of a powertrace of a specific instruction of a STM32F3 processor were described. This section is called a “template”. These templates should later be used to identify instructions via a power sidechannel and reconstruct the flow of an unknown program on a controller that can not be dumped via JTAG. In this part of our poweranalysis series the extracted templates from the previous post will be analyzed to determine whether they are representative enough to reverse engineer entire programs from a powertrace.
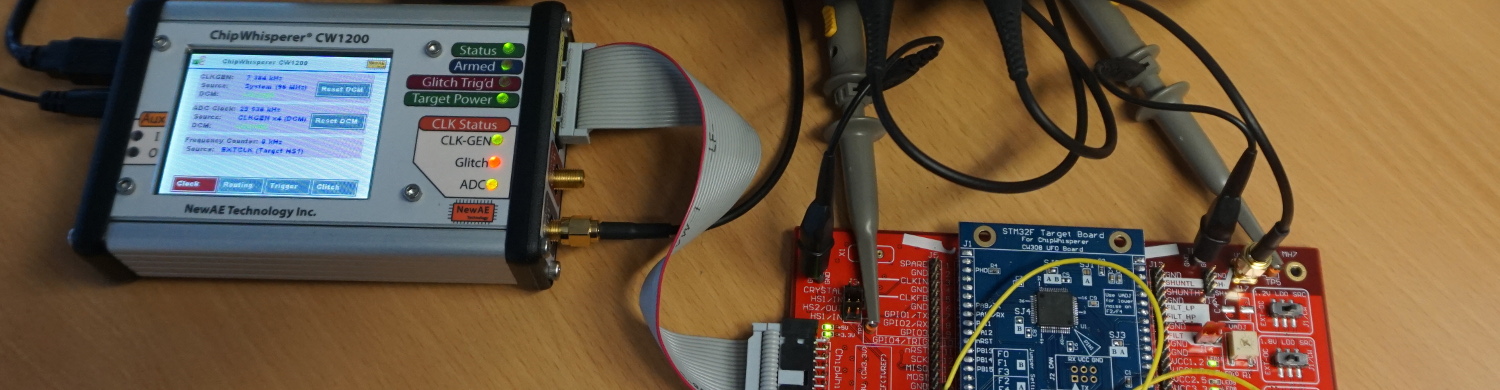
This is the first part of a three part series about power analysis based software reverse engineering. It is part of our work in the SecForCARs project and the bachelor thesis ‘Poweranalyse basiertes Software Reverse Engineering mit Hilfe von Fuzzing’. The results will be summarized in this blogpost series. In this first part the goals of the research and the power analysis template extraction process are presented.

In cooperation with the Aalen University of Applied Sciences, SCHUTZWERK organized another successful hacking event for their students. As part of the all-day event, the students were invited to solve challenges from different categories and levels of difficulty. New this year were, besides the updated Challenges in the existing areas, challenges from the topic Hardware / Embedded Security. At this point we would like to thank the University for the cooperation and congratulate the winners of the event.
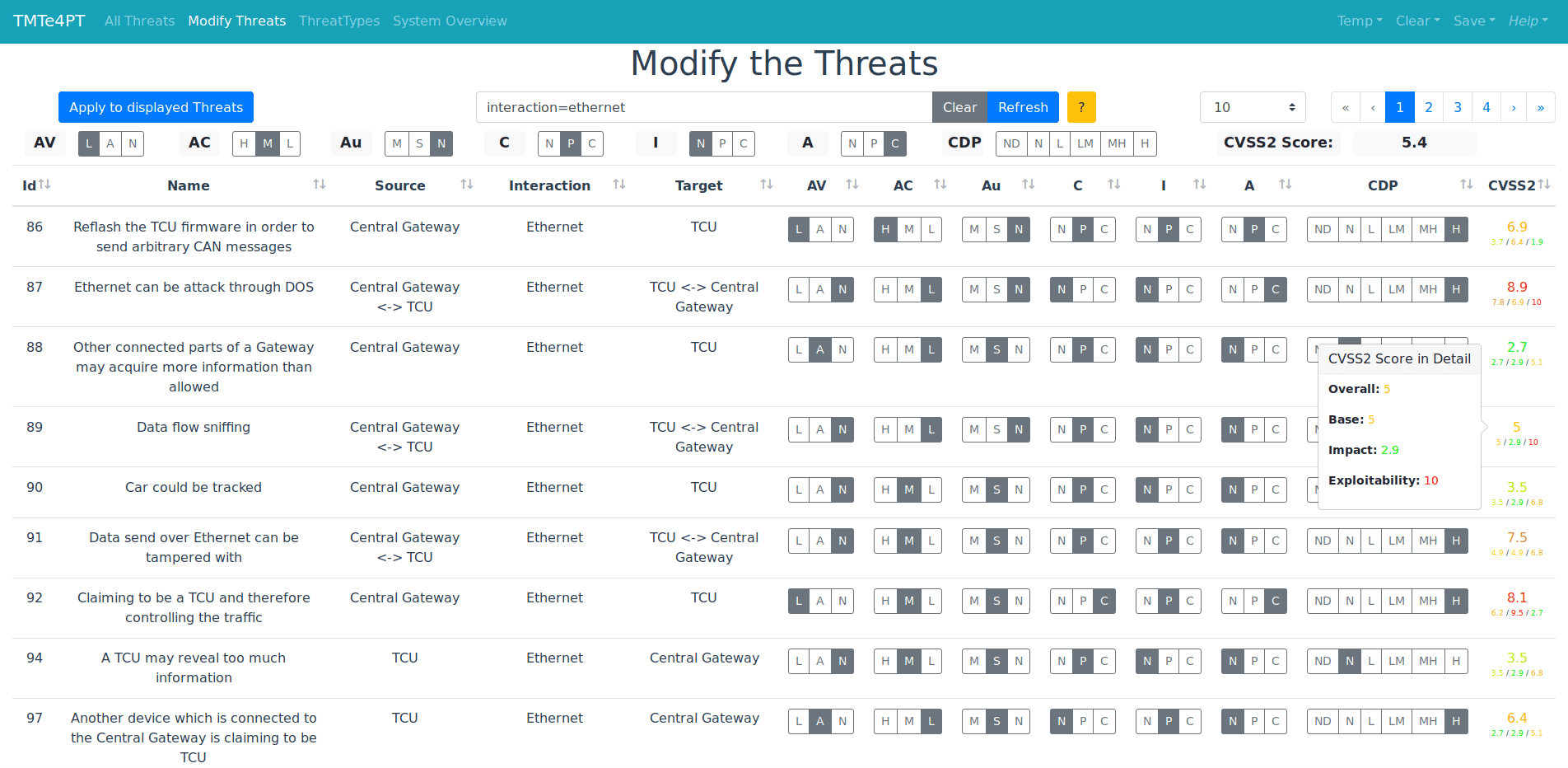
From a traditional point of view, vehicles used to be closed systems in which components communicated between each other over a central vehicle bus and no connection to remote systems was possible. However, this has drastically changed during the last years with increasing connectivity and autonomy of today’s vehicles. While car manufacturers have a long experience in dealing with safety problems, dealing with security risks raised by this development is a relatively new domain for them.

For the second year SCHUTZWERK was a sponsor of the hardwear.io conference in Den Haag. This year, we attended the conference with 3 employees focused on hardware and embedded security. The Training Session One of our hardware specialists, Heiko Ehret, learned how to reverse engineer a microchip in the training IC reverse engineering 101 from Tuesday to Wednesday. In this training the principles of gaining access to the DIE of a chip were presented and in the practical part for example photos, which were taken with a scanning electron microscope (SEM), were analyzed to extract the computational structure as well as reading out the contents of the memories.

hardwear.io will take place in Den Haag/Netherlands on 11th-13th of September 2018. SCHUTZWERK GmbH is an official sponsor of the event. hardwear.io Security Conference is a platform for hardware and security community where researchers showcase and discuss their innovative research on attacking and defending hardware. The conference will present and discuss current topics of hardware security, for example concerning automotive and IoT sectors. SCHUTZWERK regularly conducts technical assessments and security consulting in the area of embedded systems and IoT, see also Embedded Systems Assessment .
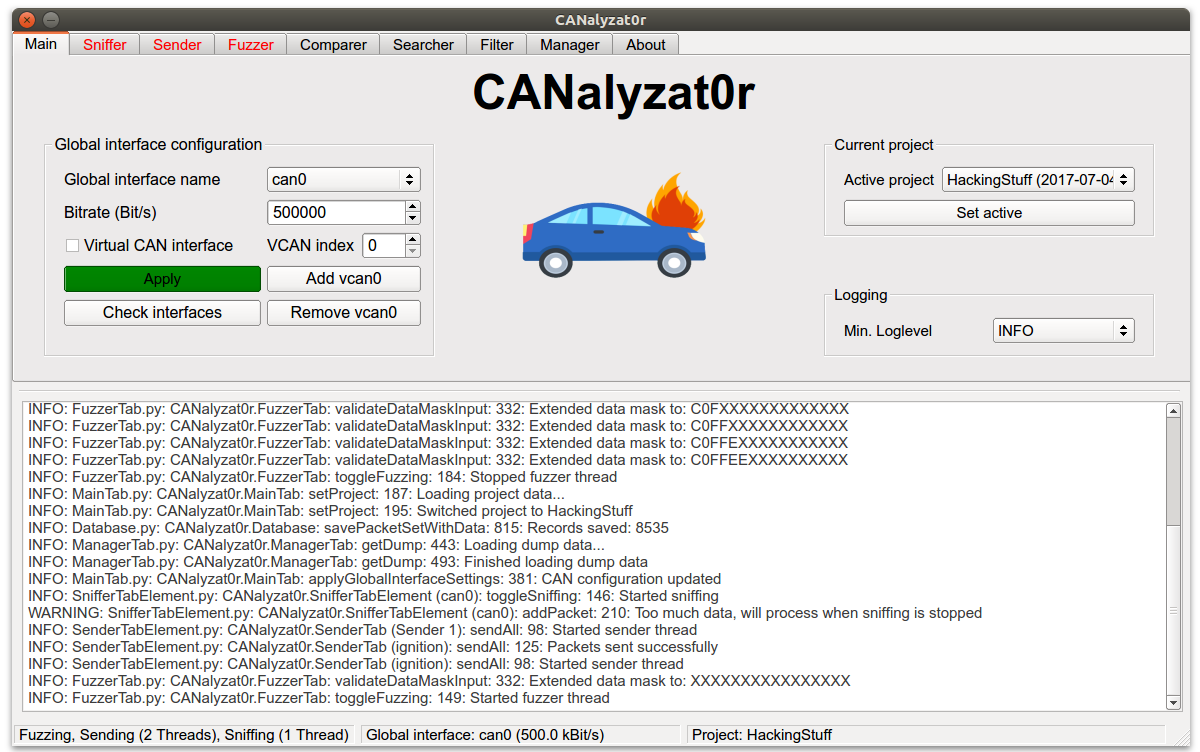
Disclaimer: The elaboration and software project associated to this subject are results of a Bachelor’s thesis created at SCHUTZWERK in collaboration with Aalen University by Philipp Schmied. While car manufacturers steadily refine and advance vehicle systems, requirements of the underlying networks increase even further. Striving for smart cars, a fast-growing amount of components are interconnected within a single car. This results in specialized and often proprietary car protocols built based on standardized technology.

hardwear.io will take place in Den Haag/Netherlands on 21st-22nd of September 2017. SCHUTZWERK GmbH is an official sponsor of the event. hardwear.io Security Conference is a platform for hardware and security community where researchers showcase and discuss their innovative research on attacking and defending hardware. The conference will present and discuss current topics of hardware security, for example concerning automotive and IoT sectors. SCHUTZWERK regularly conducts technical assessments and security consulting in the area of embedded systems and IoT, see also Embedded Systems Assessment .